Forensic Investigation: Examine Corrupt File Metadata
In this article, we will learn how we can examine a corrupt file with the help of Exiftool to get ahead in a forensic investigation.
Let’s understand a scenario
In this Scenario, a forensic investigator is stuck in a situation. He gets a suspicious folder, where no file has any kind of file extension.
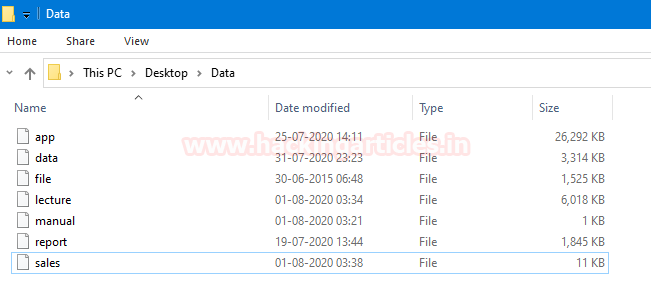
Now, he has two options.
- Examine each file’s hexadecimal values to determine the file type. To know more about this option click here.
- Extract metadata of the file.
In this article, we will cover the second option. Extract metadata of the file.
Objective: Learn to use the Exiftool metadata extractor in a forensic investigation to examine corrupt files.
Table of Content
Introduction to ExifTool
- File #1: app
- File #2: data
- File #3: file
- File #4: lecture
- File #5: manual
- File #6: report
- File #7: sales
Conclusion
Introduction to ExifTool
It is an open-source software to reading, writing, and manipulating [image, audio, video, and PDF metadata]. Which is developed by Phil Harvey. It is platform-independent based on Perl library plus a command-line application.
It supports different-different metadata formats including GPS, IPTC, EXIF, XMP, JFIF, ID3, etc. It also gets some maker notes of many digital cameras.
It is also available for Windows and macOS package, that does not require Perl setup. We just need to download and unzip the archives then double click on a file to load the software.
We can download this software from here.
File #1: app
The First file we got is app. Now, all we need to get its metadata drag and drop this corrupt file on the ExifTool .exe file. which name is ‘exiftool(-k).exe’ in the archive file which we just unzipped.
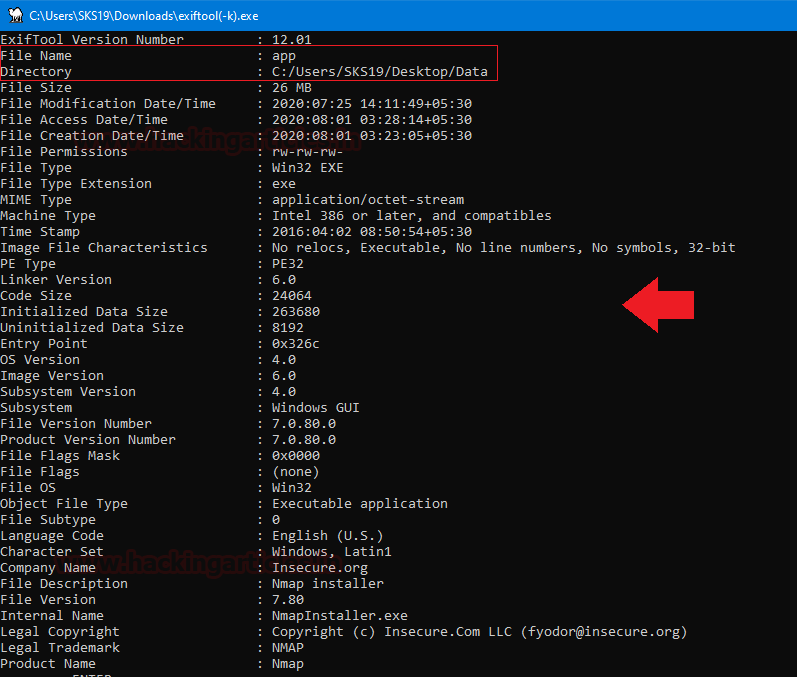
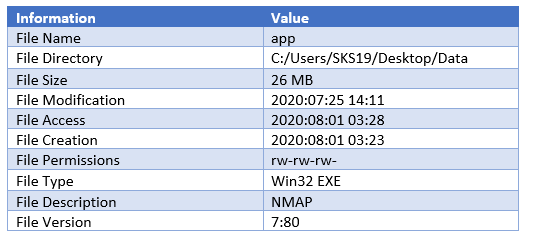
As we have captured a few interesting details in this screenshot which helps us in our forensic investigation.
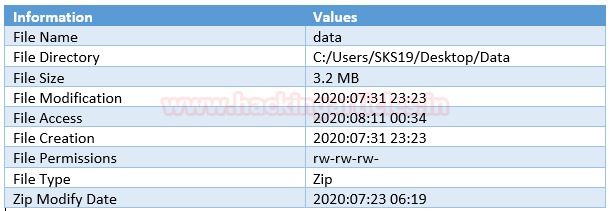
File #2: data
The Second file we got is data. Repeat the previous step, to get metadata of this file drag and drop this corrupt file on the [exiftool(-k).exe] in the archive file which we just unzipped.
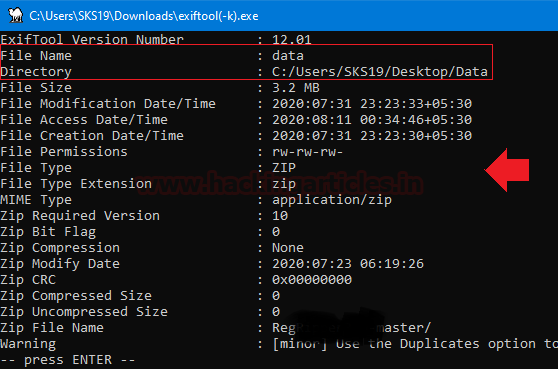
These are the few highlights of this file, which we captured for this investigation process.
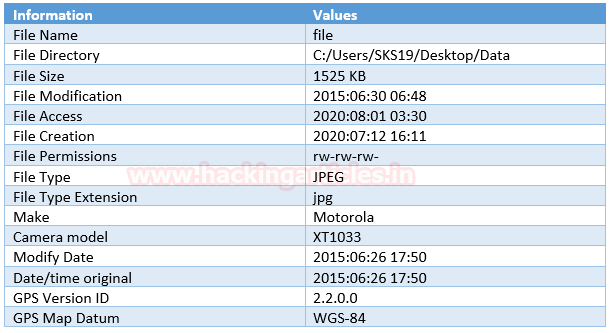
File #3: file
The Third file we got is the file. Repeat the previous step, to get metadata of this file drag and drop this corrupt file on the [exiftool(-k).exe] in the archive file which we just unzipped.

Now, few more interesting details regarding this file.
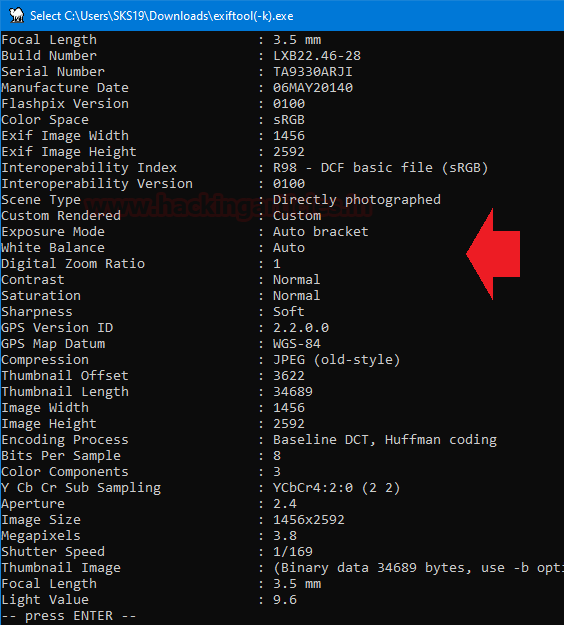
As we have captured a few interesting details in these screenshots which helps us in our forensic investigation.
File #4: lecture
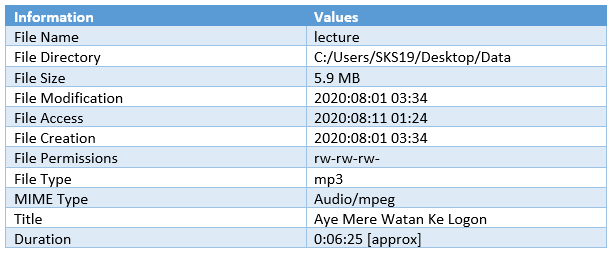
The fourth file we got is the lecture. Repeat the previous step, to get metadata of this file drag and drop this corrupt file on the [exiftool(-k).exe] in the archive file which we just unzipped.

These are the few highlights of this file, which we captured for this investigation process.
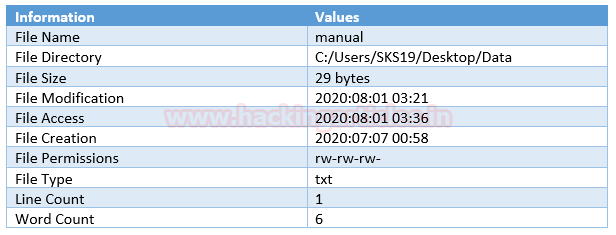
File #5: manual
The fifth file we got is the manual. Repeat the previous step, to get metadata of this file drag and drop this corrupt file on the [exiftool(-k).exe] in the archive file which we just unzipped.
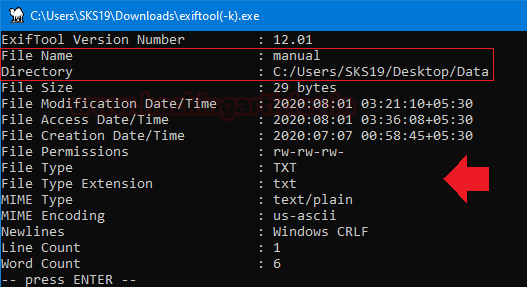
As we have captured a few interesting details in this screenshot which helps us in forensic investigation.
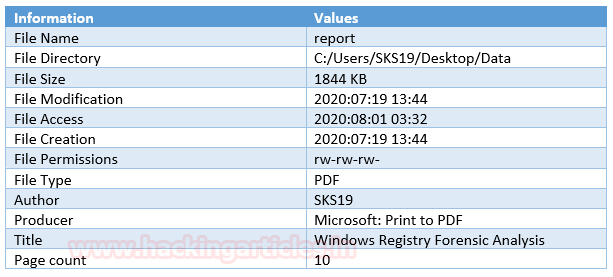
File #6: report
The Second last file we got is the report. Repeat the above steps just drag and drop this corrupted file on to [exiftool(-k).exe] to get its metadata details.
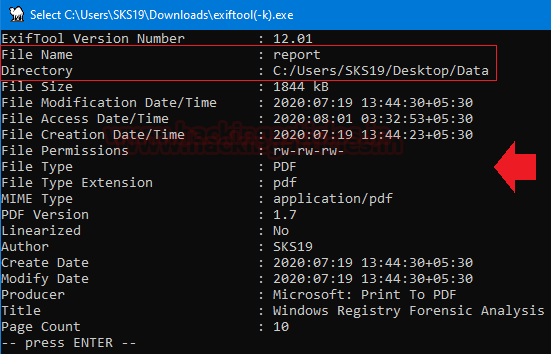
These are the few highlights of this file, which we captured for this investigation process.
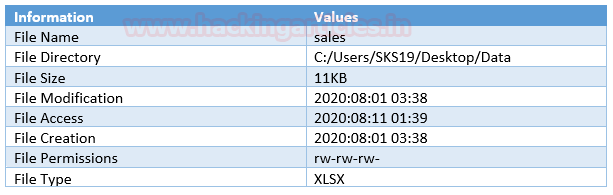
File #7: sales
The last file we got is sales. Repeat the above steps just drag and drop this corrupted file on to [exiftool(-k).exe] to get its metadata details.
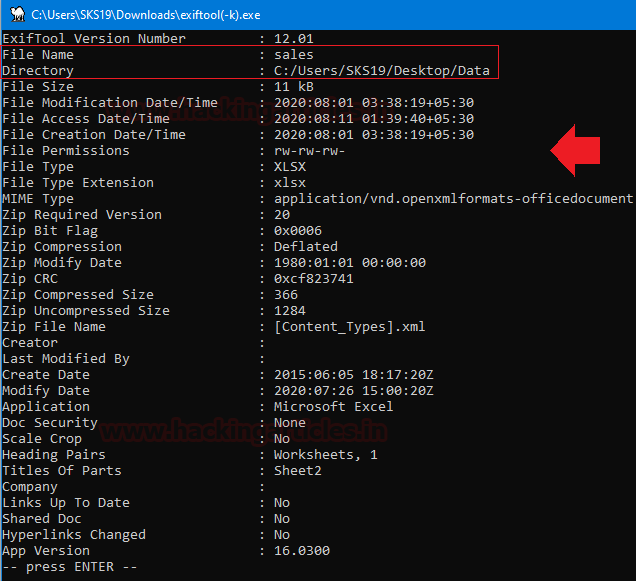
As we have captured a few interesting details in this screenshot which helps us in our forensic investigation.
Conclusion
Overall Exiftool can become quite handy in these kinds of Forensic Investigation, where a Forensic Investigator doesn’t have any clue about the file types. This method can help him to proceed further in the Investigation.
Author: Shubham Sharma is a Pentester and Cybersecurity Researcher, Contact Linkedin and twitter.